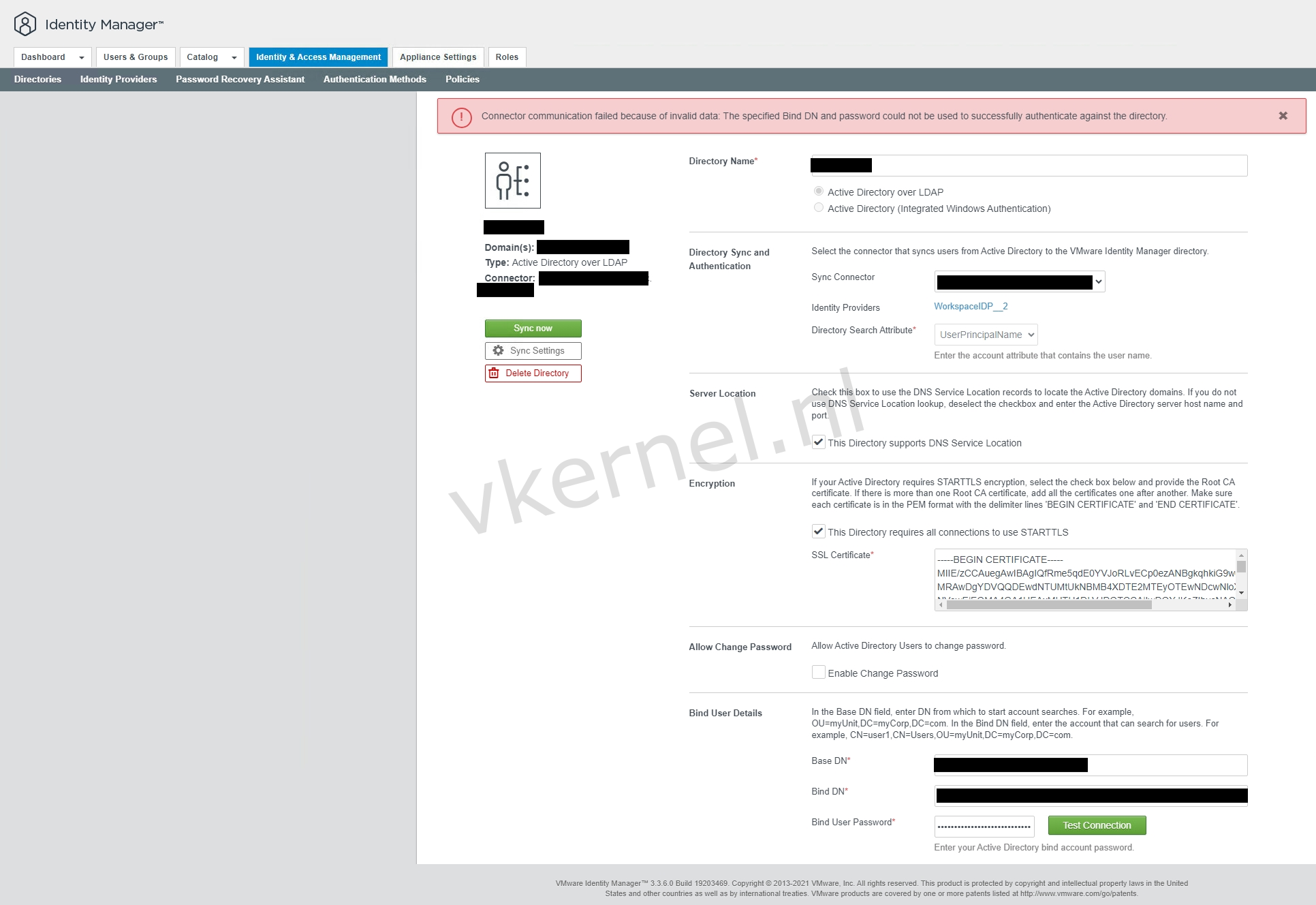
The VMware Identity Manager (vIDM) was running fine for a while until we received a mail notification from the vIDM appliance stating that the directory sync is failing with the following error message: "The specified Bind DN and password could not be used to successfully authenticate against the directory".
Investigating the issue
I wanted to verify if the issue still exists, so I performed the manual 'Sync Now' task in the directory experiencing the problem. Unfortunately, the directory sync failed with the same error message.
Directory sync failed: "The specified Bind DN and password could not be used to successfully authenticate against the directory"
Checking log files
The authentication issue could be caused by many factors and the error message is not really helping. Let's see if we can find more information in the log files on the vIDM appliance.
Start by logging in with SSH on the vIDM appliance and go to the workspace log directory as mentioned below
cd /opt/vmware/horizon/workspace/logs/
Let's start a tail on the connector.log file and reproduce the issue in through the web GUI by clicking on the 'Sync Now' button in the directory having the issue.
tail -f connector.log
The console will output the newest log entries in the connector.log file.
I have marked the error in the output red.
2023-06-30T09:38:04,290 ERROR (Thread-7) [VMID-0-01;admin@VMID-0-01;127.0.0.1;] com.vmware.horizon.connector.admin.controller.DirectoryController - Error occurred while verifying the Directory configuration.
com.vmware.horizon.connector.exception.ConfigurationVerificationException: Unable to bind to the directory
at com.vmware.horizon.connector.admin.ConfigurationVerificationServiceImpl.verifyDirectory(ConfigurationVerificationServiceImpl.java:124) ~[classes/:3.3.6.0 Build 19203469]
at com.vmware.horizon.connector.admin.controller.DirectoryController.verifyDirectoryConfigurationAgainstActiveDirectory(DirectoryController.java:264) [classes/:3.3.6.0 Build 19203469]
at com.vmware.horizon.connector.admin.controller.DirectoryController.testDirectoryConfiguration(DirectoryController.java:252) [classes/:3.3.6.0 Build 19203469]
at com.vmware.horizon.connector.admin.controller.DirectoryController$$FastClassBySpringCGLIB$$22197277.invoke(<generated>) [classes/:3.3.6.0 Build 19203469]
at org.springframework.cglib.proxy.MethodProxy.invoke(MethodProxy.java:218) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.aop.framework.CglibAopProxy$DynamicAdvisedInterceptor.intercept(CglibAopProxy.java:687) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.connector.admin.controller.DirectoryController$$EnhancerBySpringCGLIB$$d818957c.testDirectoryConfiguration(<generated>) [classes/:3.3.6.0 Build 19203469]
at com.vmware.horizon.connector.rest.DirectoryRestController.testDirectoryConfig(DirectoryRestController.java:150) [classes/:3.3.6.0 Build 19203469]
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method) ~[?:1.8.0_292]
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62) ~[?:1.8.0_292]
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) ~[?:1.8.0_292]
at java.lang.reflect.Method.invoke(Method.java:498) ~[?:1.8.0_292]
at org.springframework.web.method.support.InvocableHandlerMethod.doInvoke(InvocableHandlerMethod.java:190) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.method.support.InvocableHandlerMethod.invokeForRequest(InvocableHandlerMethod.java:138) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.servlet.mvc.method.annotation.ServletInvocableHandlerMethod.invokeAndHandle(ServletInvocableHandlerMethod.java:105) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerAdapter.invokeHandlerMethod(RequestMappingHandlerAdapter.java:878) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerAdapter.handleInternal(RequestMappingHandlerAdapter.java:792) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.servlet.mvc.method.AbstractHandlerMethodAdapter.handle(AbstractHandlerMethodAdapter.java:87) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.servlet.DispatcherServlet.doDispatch(DispatcherServlet.java:1040) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.servlet.DispatcherServlet.doService(DispatcherServlet.java:943) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.servlet.FrameworkServlet.processRequest(FrameworkServlet.java:1006) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.servlet.FrameworkServlet.doPost(FrameworkServlet.java:909) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at javax.servlet.http.HttpServlet.service(HttpServlet.java:652) [servlet-api.jar:?]
at org.springframework.web.servlet.FrameworkServlet.service(FrameworkServlet.java:883) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at javax.servlet.http.HttpServlet.service(HttpServlet.java:733) [servlet-api.jar:?]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) [catalina.jar:8.5.63]
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52) [tomcat-websocket.jar:8.5.63]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) [catalina.jar:8.5.63]
at com.vmware.horizon.connector.mvc.FlashScopeFilter.doFilterInternal(FlashScopeFilter.java:45) [classes/:3.3.6.0 Build 19203469]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) [catalina.jar:8.5.63]
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:209) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:178) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:358) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:271) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) [catalina.jar:8.5.63]
at org.springframework.web.filter.CharacterEncodingFilter.doFilterInternal(CharacterEncodingFilter.java:201) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:119) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) [catalina.jar:8.5.63]
at com.vmware.horizon.common.filter.TenantContextFilter.doFilter(TenantContextFilter.java:108) [horizon-request-utils-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:358) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:271) [kdc-kerberos-auth-adapter-0.1.jar:3.3.6.0 Build 19203469]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationDispatcher.invoke(ApplicationDispatcher.java:711) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationDispatcher.processRequest(ApplicationDispatcher.java:460) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationDispatcher.doForward(ApplicationDispatcher.java:387) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationDispatcher.forward(ApplicationDispatcher.java:315) [catalina.jar:8.5.63]
at org.tuckey.web.filters.urlrewrite.NormalRewrittenUrl.doRewrite(NormalRewrittenUrl.java:213) [urlrewritefilter-4.0.4.jar:4.0.4]
at org.tuckey.web.filters.urlrewrite.RuleChain.handleRewrite(RuleChain.java:171) [urlrewritefilter-4.0.4.jar:4.0.4]
at org.tuckey.web.filters.urlrewrite.RuleChain.doRules(RuleChain.java:145) [urlrewritefilter-4.0.4.jar:4.0.4]
at org.tuckey.web.filters.urlrewrite.UrlRewriter.processRequest(UrlRewriter.java:92) [urlrewritefilter-4.0.4.jar:4.0.4]
at org.tuckey.web.filters.urlrewrite.UrlRewriteFilter.doFilter(UrlRewriteFilter.java:389) [urlrewritefilter-4.0.4.jar:4.0.4]
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) [catalina.jar:8.5.63]
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) [catalina.jar:8.5.63]
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:199) [catalina.jar:8.5.63]
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:97) [catalina.jar:8.5.63]
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:544) [catalina.jar:8.5.63]
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:143) [catalina.jar:8.5.63]
at com.vmware.horizon.catalina.PortRedirectionValve.invoke(PortRedirectionValve.java:76) [horizon-catalina-0.1.jar:3.3.5.0 Build 18380290]
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:81) [catalina.jar:8.5.63]
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:698) [catalina.jar:8.5.63]
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:78) [catalina.jar:8.5.63]
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:353) [catalina.jar:8.5.63]
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:616) [tomcat-coyote.jar:8.5.63]
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) [tomcat-coyote.jar:8.5.63]
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) [tomcat-coyote.jar:8.5.63]
at org.apache.tomcat.util.net.Nio2Endpoint$SocketProcessor.doRun(Nio2Endpoint.java:1615) [tomcat-coyote.jar:8.5.63]
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) [tomcat-coyote.jar:8.5.63]
at org.apache.tomcat.util.net.AbstractEndpoint.processSocket(AbstractEndpoint.java:1107) [tomcat-coyote.jar:8.5.63]
at org.apache.tomcat.util.net.Nio2Endpoint$Nio2SocketWrapper$2.completed(Nio2Endpoint.java:564) [tomcat-coyote.jar:8.5.63]
at org.apache.tomcat.util.net.Nio2Endpoint$Nio2SocketWrapper$2.completed(Nio2Endpoint.java:542) [tomcat-coyote.jar:8.5.63]
at org.apache.tomcat.util.net.SecureNio2Channel$1.completed(SecureNio2Channel.java:989) [tomcat-coyote.jar:8.5.63]
at org.apache.tomcat.util.net.SecureNio2Channel$1.completed(SecureNio2Channel.java:918) [tomcat-coyote.jar:8.5.63]
at sun.nio.ch.Invoker.invokeUnchecked(Invoker.java:126) [?:1.8.0_292]
at sun.nio.ch.UnixAsynchronousSocketChannelImpl.finishRead(UnixAsynchronousSocketChannelImpl.java:432) [?:1.8.0_292]
at sun.nio.ch.UnixAsynchronousSocketChannelImpl.finish(UnixAsynchronousSocketChannelImpl.java:191) [?:1.8.0_292]
at sun.nio.ch.UnixAsynchronousSocketChannelImpl.onEvent(UnixAsynchronousSocketChannelImpl.java:213) [?:1.8.0_292]
at sun.nio.ch.EPollPort$EventHandlerTask.run(EPollPort.java:293) [?:1.8.0_292]
at sun.nio.ch.AsynchronousChannelGroupImpl$1.run(AsynchronousChannelGroupImpl.java:112) [?:1.8.0_292]
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) [?:1.8.0_292]
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) [?:1.8.0_292]
at java.lang.Thread.run(Thread.java:748) [?:1.8.0_292]
Caused by: com.vmware.horizon.directory.DirectoryServiceException: Unknown runtime error occurred
at com.vmware.horizon.directory.ldap.dc.service.context.StartTLSContextFetcher.fetchContext(StartTLSContextFetcher.java:52) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.dc.service.DirectoryConnectService.getLdapContextForDirectoryWithProvidedADHost(DirectoryConnectService.java:57) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.dc.service.DirectoryConnectService.getLdapContextForDirectoryWithoutProvidedADHost(DirectoryConnectService.java:79) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.LdapConnector.createLdapContext(LdapConnector.java:1408) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.LdapConnector.createLdapContextWithOptimalDomainController(LdapConnector.java:1381) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.connector.admin.ConfigurationVerificationServiceImpl.verifyDirectory(ConfigurationVerificationServiceImpl.java:121) ~[classes/:3.3.6.0 Build 19203469]
... 87 more
Caused by: javax.net.ssl.SSLHandshakeException
at sun.security.ssl.Alert.createSSLException(Alert.java:131) ~[?:1.8.0_292]
at sun.security.ssl.TransportContext.fatal(TransportContext.java:348) ~[?:1.8.0_292]
at sun.security.ssl.TransportContext.fatal(TransportContext.java:291) ~[?:1.8.0_292]
at sun.security.ssl.TransportContext.fatal(TransportContext.java:286) ~[?:1.8.0_292]
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.checkServerCerts(CertificateMessage.java:654) ~[?:1.8.0_292]
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.onCertificate(CertificateMessage.java:473) ~[?:1.8.0_292]
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.consume(CertificateMessage.java:369) ~[?:1.8.0_292]
at sun.security.ssl.SSLHandshake.consume(SSLHandshake.java:377) ~[?:1.8.0_292]
at sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:444) ~[?:1.8.0_292]
at sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:422) ~[?:1.8.0_292]
at sun.security.ssl.TransportContext.dispatch(TransportContext.java:182) ~[?:1.8.0_292]
at sun.security.ssl.SSLTransport.decode(SSLTransport.java:156) ~[?:1.8.0_292]
at sun.security.ssl.SSLSocketImpl.decode(SSLSocketImpl.java:1409) ~[?:1.8.0_292]
at sun.security.ssl.SSLSocketImpl.readHandshakeRecord(SSLSocketImpl.java:1315) ~[?:1.8.0_292]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:439) ~[?:1.8.0_292]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:410) ~[?:1.8.0_292]
at com.sun.jndi.ldap.ext.StartTlsResponseImpl.startHandshake(StartTlsResponseImpl.java:354) ~[?:1.8.0_292]
at com.sun.jndi.ldap.ext.StartTlsResponseImpl.negotiate(StartTlsResponseImpl.java:217) ~[?:1.8.0_292]
at com.vmware.horizon.directory.ldap.dc.service.context.StartTLSContextFetcher.extendToSecureMode(StartTLSContextFetcher.java:61) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.dc.service.context.StartTLSContextFetcher.fetchContext(StartTLSContextFetcher.java:48) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.dc.service.DirectoryConnectService.getLdapContextForDirectoryWithProvidedADHost(DirectoryConnectService.java:57) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.dc.service.DirectoryConnectService.getLdapContextForDirectoryWithoutProvidedADHost(DirectoryConnectService.java:79) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.LdapConnector.createLdapContext(LdapConnector.java:1408) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.LdapConnector.createLdapContextWithOptimalDomainController(LdapConnector.java:1381) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.connector.admin.ConfigurationVerificationServiceImpl.verifyDirectory(ConfigurationVerificationServiceImpl.java:121) ~[classes/:3.3.6.0 Build 19203469]
... 87 more
Caused by: java.security.cert.CertificateException
at com.vmware.horizon.dirsync.ExplicitX509TrustManager.checkServerTrusted(ExplicitX509TrustManager.java:108) ~[commons-connector-0.1.jar:3.3.6.0 Build 19203469]
at sun.security.ssl.AbstractTrustManagerWrapper.checkServerTrusted(SSLContextImpl.java:1256) ~[?:1.8.0_292]
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.checkServerCerts(CertificateMessage.java:638) ~[?:1.8.0_292]
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.onCertificate(CertificateMessage.java:473) ~[?:1.8.0_292]
at sun.security.ssl.CertificateMessage$T12CertificateConsumer.consume(CertificateMessage.java:369) ~[?:1.8.0_292]
at sun.security.ssl.SSLHandshake.consume(SSLHandshake.java:377) ~[?:1.8.0_292]
at sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:444) ~[?:1.8.0_292]
at sun.security.ssl.HandshakeContext.dispatch(HandshakeContext.java:422) ~[?:1.8.0_292]
at sun.security.ssl.TransportContext.dispatch(TransportContext.java:182) ~[?:1.8.0_292]
at sun.security.ssl.SSLTransport.decode(SSLTransport.java:156) ~[?:1.8.0_292]
at sun.security.ssl.SSLSocketImpl.decode(SSLSocketImpl.java:1409) ~[?:1.8.0_292]
at sun.security.ssl.SSLSocketImpl.readHandshakeRecord(SSLSocketImpl.java:1315) ~[?:1.8.0_292]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:439) ~[?:1.8.0_292]
at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:410) ~[?:1.8.0_292]
at com.sun.jndi.ldap.ext.StartTlsResponseImpl.startHandshake(StartTlsResponseImpl.java:354) ~[?:1.8.0_292]
at com.sun.jndi.ldap.ext.StartTlsResponseImpl.negotiate(StartTlsResponseImpl.java:217) ~[?:1.8.0_292]
at com.vmware.horizon.directory.ldap.dc.service.context.StartTLSContextFetcher.extendToSecureMode(StartTLSContextFetcher.java:61) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.dc.service.context.StartTLSContextFetcher.fetchContext(StartTLSContextFetcher.java:48) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.dc.service.DirectoryConnectService.getLdapContextForDirectoryWithProvidedADHost(DirectoryConnectService.java:57) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.dc.service.DirectoryConnectService.getLdapContextForDirectoryWithoutProvidedADHost(DirectoryConnectService.java:79) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.LdapConnector.createLdapContext(LdapConnector.java:1408) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.directory.ldap.LdapConnector.createLdapContextWithOptimalDomainController(LdapConnector.java:1381) ~[adapter-ldap-0.1.jar:3.3.6.0 Build 19203469]
at com.vmware.horizon.connector.admin.ConfigurationVerificationServiceImpl.verifyDirectory(ConfigurationVerificationServiceImpl.java:121) ~[classes/:3.3.6.0 Build 19203469]
... 87 more
Validating root certificate
In the output, we see that the issue is caused during the SSL handshake certificate validation. So, this points me to the root certificate that has been configured on the vIDM appliance. The configured root certificate can be found in the web GUI of the vIDM appliance under the Encryption section in the directory settings.
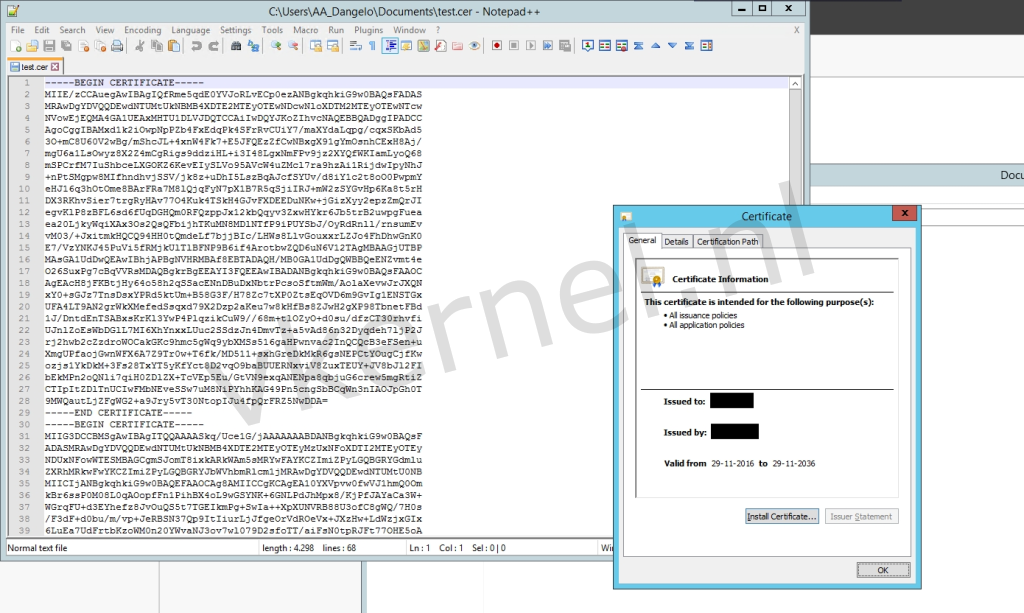
Copy the content and save it to a file with the extension .cer. Then, open this file in Windows to view the certificate details.
I confirmed that the root certificate is not expired by checking the Valid from field of the certificate and also made a note of its serial number.
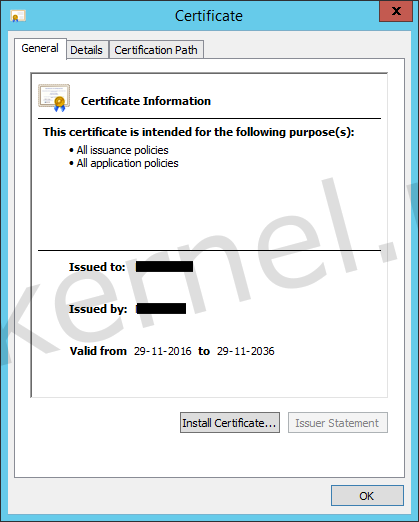
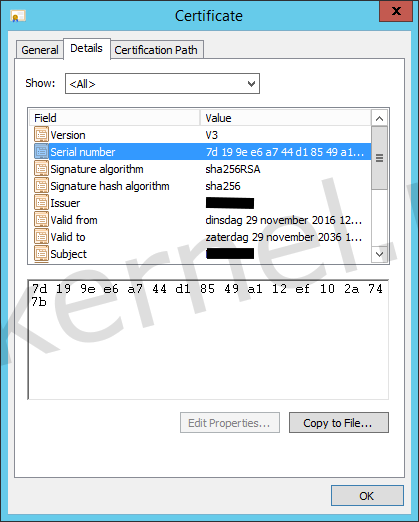
I wanted to see if the root certificate was matching the root certificate of the domain, so I exported the root certificate from the Windows domain. The steps to export the root certificate from a Windows domain can be found here.
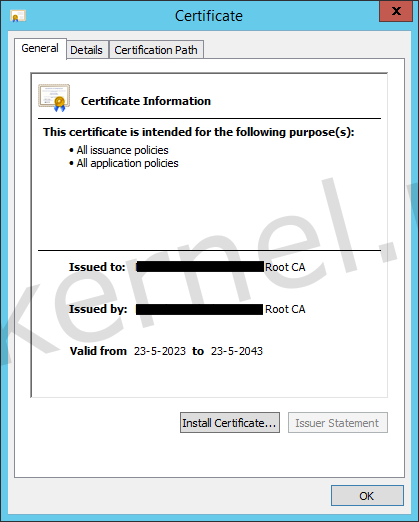
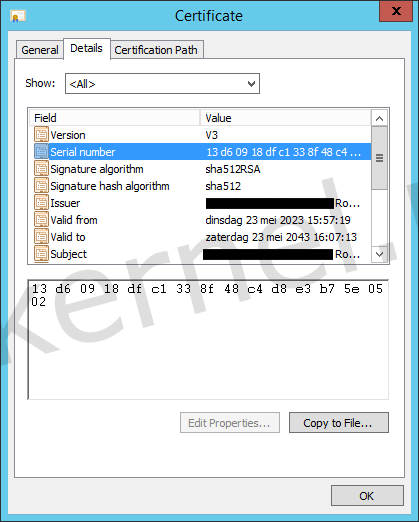
To my surprise, I found out that the exported root certificate was different than the certificate that was configured on the vIDM appliance. The Issuer, Subject and Serial number didn't matched.
|  |
|  |
|
Resolution
The issue was fixed by updating the root certificate under the Encryption section of the directory that had the issue. The Sync Now task is running succesfully and the directory is in sync again.
Checking the log files often provides additional information about the error message, so being familiar with investigating log files through an SSH session is key. if you have any questions, do not hesistate to reach out to me.